The Digital Maze: How Unusual Network Activity Mirrors Modern Business Challenges
At first glance, a message prompting you to verify you’re not a robot might seem like a minor irritation in our fast-paced digital world. However, this seemingly small task reflects a broader narrative about the increasingly intertwined nature of technology, cybersecurity, and business operations. Whether you’re running a small business, overseeing industrial manufacturing, navigating the complexities of automotive and electric vehicle technology, or interpreting economic news and changes in business tax laws, the system of online verifications reveals a maze of tricky parts that many business leaders are currently working through.
The message that says, “We’ve detected unusual activity from your computer network,” and then requests you to confirm your humanity is more than a mere inconvenience. It encapsulates the challenges inherent in today’s digital ecosystem and the impacts they have across multiple sectors. In this editorial, we’ll take a closer look at how these online security measures are not only safeguarding data but are also entwined with broader business dynamics. We’ll examine the tangled issues being faced by various industries and offer perspectives on how to figure a path through these new digital requirements.
Understanding Unusual Network Activity: A Window into Modern Cybersecurity
When your computer network is flagged for unusual activity, it isn’t simply a case of a system glitch. Instead, it represents the organized efforts of tech companies and security experts to protect both consumers and businesses from the perils of online threats. In our daily digital transactions, whether we’re making a quick online purchase or accessing confidential business data, the background processes working to keep our online environments safe must manage a series of complicated pieces and hidden challenges.
Many of the validation measures—like ensuring your browser supports JavaScript and cookies—are designed to thwart automated systems from breaching secured spaces. While these checks can sometimes slow down a user’s access, they form a critical layer of defense against digital mischief. It is a reminder of how even routine online interactions are steeped in a network of security protocols, each with its own set of fine points and subtle parts that serve to protect our sensitive information.
Small Business Online Security: The Subtle Details That Can Make or Break Success
For small business owners, this digital verification process is more than an annoyance—it’s a snapshot of a larger, nerve-racking landscape. Small business digital security must balance speed, convenience, and a high level of protection. When a seemingly minor hurdle like a captcha or similar security prompt causes delays, it raises concerns about customer experience and the overall impression of a company’s online presence.
Challenges Faced by Small Businesses
Small business owners often work with limited resources and must manage multiple duties simultaneously. The added load of ensuring digital security in an era filled with phishing scams and data breaches can feel overwhelming. Consider the following points:
- Delayed Customer Interactions: When site visitors are pitched with verification steps, it may cause frustration and even lead to abandoned transactions.
- Maintenance Costs: Implementing sophisticated cybersecurity measures can strain limited budgets, especially when unexpected issues arise.
- Technology Gaps: Not all small businesses have the luxury of expert IT teams, leaving owners to figure a path through a maze of tricky digital solutions.
Strategies for Working Through Security Challenges
Despite these hurdles, there are several ways small business owners can build resilient digital strategies without overwhelming their operations:
- Investing in User-Friendly Security Tools: Software that gracefully integrates security checks within the user interface reduces the risk of customer drop-off.
- Continuous Employee Training: A well-informed team, aware of the little twists and subtle parts of cybersecurity, can better manage potential vulnerabilities.
- Outsourcing IT Support: Engaging external experts on a need basis can ease the financial and operational burden of managing cybersecurity in-house.
Table 1 provides a quick overview of challenges and their potential solutions for small business online security.
| Challenge | Potential Solution |
|---|---|
| Delayed customer interactions | User-friendly security interfaces and streamlined verification processes |
| High maintenance costs | Leverage cost-effective cybersecurity solutions and scalable security services |
| Insufficient in-house expertise | Outsource technical support to dedicated cybersecurity professionals |
Industrial Manufacturing Cybersecurity: Keeping Production Lines Secure
In the realm of industrial manufacturing, digital security is not just about protecting sensitive business information—it’s also about ensuring that production lines run smoothly. Factories and plants worldwide integrate networked systems for everything from inventory control to robotics. When these systems encounter security verifications or unexpected alerts, they highlight the hidden complexities inherent in managing large-scale technological infrastructures.
Digital Integration in Industrial Manufacturing
Modern industrial manufacturing relies heavily on interconnected systems. This digital integration can optimize production efficiency but also introduces new challenges, including:
- Operational Downtime: Unexpected security checks or false alarms can temporarily halt production, leading to expensive downtimes.
- System Vulnerabilities: Unsecured or poorly maintained systems may be exploited by hackers, posing threats to production safety and efficiency.
- Data Integrity Issues: Maintaining the accuracy and security of production data is key, but often comes with a host of tricky parts related to data management and transfers.
Enhancing Cybersecurity in Manufacturing
As the manufacturing sector continues to fuse digital technologies into its operations, these companies must ensure that their cyber defenses are as robust as possible. Here are some options:
- Automated Security Systems: Implementing automated systems that monitor and flag unusual activity can help production managers get into issues before they escalate.
- Regular System Audits: Frequent checks and system audits can help companies find their way around potential vulnerabilities and ensure that any digital disruption is minimized.
- Employee Awareness Programs: Workers on the shop floor must recognize subtle signs of system failure or cyber threats, ensuring a proactive approach to security.
Industrial manufacturing leaders must therefore work through the maze of online security and integration issues to safeguard their operations. Failure to do so could not only compromise sensitive industrial data but also lead to costly interruptions in production.
Automotive and Electric Vehicle Technology: Bridging High-Tech Security and Consumer Trust
The world of automotive and electric vehicles is evolving at breakneck speed. Modern vehicles are not only pieces of machinery but also sophisticated computers on wheels, connected to vast networks for navigation, performance tracking, and even remote diagnostics. With this technological prowess comes an increased responsibility to manage and protect these systems.
Cybersecurity Challenges in High-Tech Vehicles
As automotive models integrate more advanced digital features, manufacturers face a series of complicated pieces in ensuring that all on-board systems are immune to hacking attempts or unauthorized access. Such challenges include:
- Remote Hacking Risks: Hackers targeting vehicle systems can disrupt operations or compromise personal data if security measures fail.
- Data Privacy Concerns: With vehicles continuously collecting data, ensuring that information remains secure and private is critical.
- Integration with Consumer Devices: As vehicles interact seamlessly with personal electronics and mobile devices, the overall cybersecurity framework is only as strong as its weakest interface.
Building Trust Through Robust Cybersecurity
Automotive manufacturers have taken significant steps to reinforce digital security in vehicles. By employing layered security protocols and continuously updating system software, these companies exemplify how to steer through a maze of complicated issues while maintaining consumer trust and safety. As autonomous and electric vehicles become increasingly mainstream, the effectiveness of these cybersecurity measures will play a pivotal role in market acceptance and regulatory approval.
Moreover, the transition to electric vehicles brings with it not only environmental advantages but also unique challenges. Compared to traditional combustion engines, electric vehicles often incorporate even more advanced digital ecosystems. As such, ensuring these systems are secure and free from vulnerabilities is super important—making the intersection of cybersecurity and automotive innovation a field worth careful attention.
Business Tax Laws and Global Economic Updates: When Digital Security Meets Fiscal Strategy
Beyond the technological spheres of manufacturing and automotive industries, digital security has significant implications for business tax laws and economic policy. Over the past decade, economic news across the globe has underscored a marked increase in cybersecurity spending by businesses, an expense that is intricately linked with overall economic performance.
The Economic Impact of Cybersecurity Investments
When businesses allocate resources to cybersecurity, they are in effect making a key investment in the durability and performance of their operations. For small businesses and large multinational corporations alike, the cost of implementing robust digital security systems is balanced against the potentially devastating financial impact of cyber-attacks. Some considerations include:
- Tax Deductions: Many jurisdictions now allow businesses to claim tax deductions for cybersecurity investments, providing a financial buffer for companies investing in these measures.
- Boosting Investor Confidence: Firms that are well-protected against cyber threats often enjoy enhanced trust from both investors and customers, translating into improved market performance.
- Mitigating Liability Risks: By proactively managing digital security, companies reduce the risk of data breaches and the subsequent legal and financial consequences.
Marketing Strategies in the Age of Digital Security
In today’s digital landscape, marketing strategies must also account for the impact of cybersecurity protocols on customer engagement. Every additional security prompt, such as verifying a user’s humanity, affects the customer journey. Marketing teams must carefully work through the balance between security and usability, ensuring that the online experience remains smooth while preserving essential protection.
Modern marketing approaches often emphasize the following:
- User Experience Optimization: Ensuring that security checkpoints are streamlined to avoid unnecessary friction during the customer journey.
- Transparency in Privacy Policies: Clear communication regarding how customer data is protected can bolster trust and loyalty.
- Adapting to Regulatory Requirements: As data protection laws evolve globally, businesses must quickly adapt their marketing messages and operational protocols to remain compliant.
The interplay between digital security and fiscal policy is a dynamic one. With global economic updates frequently highlighting the growing importance of cyber resilience, companies must figure a path that integrates smart cybersecurity investments with broader business strategy—ensuring that the financial and operational aspects of the business are continuously aligned with emerging regulatory landscapes.
Integrating Security Protocols in Diverse Sectors: Lessons from a Digital World
Across small business, industrial manufacturing, automotive innovation, and even tax law compliance, the need to get into security protocols and manage their impacts is universal. The challenge isn’t simply in implementing advanced digital safeguards; it’s about doing so in a manner that minimizes disruptions and fosters enduring trust among users, customers, and stakeholders.
Key Takeaways for Business Leaders
While the digital verification messages might seem like trivial interruptions, they carry broader symbolic meaning. They force us to address several important points:
- Adaptability: In a dynamic digital era, businesses must remain agile enough to adopt new security measures without hampering user engagement.
- Customer-Centric Design: Every security feature integrated on a website or digital platform should prioritize the user experience, reducing annoying interruptions and ensuring smooth interactions.
- Proactive Investment: Whether through outsourcing IT support or investing in the latest cybersecurity software, proactive measures are critical to shielding a business from ever-evolving threats.
A Comparative Overview: Sector-Specific Security Implications
To further highlight these points, consider the following table outlining key cybersecurity concerns and possible measures across select sectors:
| Sector | Security Concern | Suggested Approach |
|---|---|---|
| Small Business | User experience disruptions; cost constraints | Adopt streamlined security tools; leverage external IT support |
| Industrial Manufacturing | Operational downtimes; integration vulnerabilities | Implement automated monitoring; emphasize continuous audits |
| Automotive/Electric Vehicles | Remote hacking; data privacy | Layered security solutions; regular system updates |
| Fiscal Policy & Marketing | Regulatory compliance; customer trust concerns | Clear privacy policies; secure data management practices |
This broad approach to cybersecurity underscores the super important idea that digital safety isn’t a one-off project. Instead, it is an ongoing effort filled with little distinctions and hidden issues that must be continuously managed as technology evolves.
The Impact of Digital Verification on Global Economic Trends
The frequent occurrence of messages like “unusual activity detected” has far-reaching implications that extend well beyond individual user frustration. As the global economy becomes more digitally mediated, initiatives designed to protect data take on a key role in economic stability. Financial markets, international trade, and even consumer behavior are shaped by the assurance that businesses are actively safeguarding sensitive information.
Global Economic Implications
In today’s economic climate, digital security can play a decisive role in determining investor confidence and market stability. Governments and regulatory bodies increasingly focus on the reliability of digital infrastructures as a core element of national security. Moreover, businesses that can successfully figure a path through challenging security implementations—and communicate these efforts transparently—often secure a competitive edge in the global marketplace.
Key points that mirror this interplay include:
- International Trade: Trust in a company’s digital operations is crucial when engaging with international partners and suppliers.
- Market Volatility: Data breaches and cybersecurity lapses can lead to sharp market corrections, affecting not only individual companies but entire industry sectors.
- Investor Sentiment: Firms that proactively invest in robust digital security measures often experience enhanced investor confidence, which can contribute to long-term financial stability.
Role of Regulatory Agencies
Regulatory agencies are working closely with both the private sector and international partners to ensure that cybersecurity standards keep pace with innovation. As digital verification processes become more common, these agencies provide guidelines that help companies get around common pitfalls while enforcing best practices in data protection. For companies, this means that fiscal and cybersecurity compliance are not separate challenges but rather interconnected aspects of successful business management.
Marketing in a Cyber-Aware World: Engaging Customers Amid Security Protocols
Marketing strategies must also evolve in an era where digital security occupies center stage. The friction created by security prompts can seem off-putting if not managed properly, but they also offer marketers a unique opportunity to reinforce a brand’s commitment to protecting its customers.
Maintaining a Positive User Experience
Effective marketing in this landscape involves a careful balancing act between protecting user data and ensuring a fluid customer journey online. Here are a few strategies that marketing professionals might consider:
- User Education Campaigns: Informing customers about why security checks are necessary can transform a moment of inconvenience into an assurance of safety.
- Seamless Integration: Investing in technologies that integrate security protocols behind the scenes, thereby minimizing direct impact on the user experience.
- Feedback Loops: Establishing channels where customers can report and discuss timing issues or frustrations allows companies to continuously improve their digital interfaces.
This approach not only protects customer data but also reinforces the market perception of a brand as a transparent, responsible, and forward-thinking entity. Ultimately, a robust digital security framework, when communicated effectively, becomes a part of the company’s marketing story.
Future Outlook: Adapting to an Ever-Evolving Cybersecurity Landscape
Looking ahead, the digital landscape is poised to become even more full of problems and loaded with issues, requiring businesses in every field—from small enterprises to multinational conglomerates—to work through security challenges with creative, flexible strategies. We are likely to see:
- Increased Investment in Cybersecurity: As cyber threats proliferate, more funds will be allocated to both technology and training that secure online operations.
- Advanced Verification Technologies: Innovations such as biometric verifications, AI-powered threat detection, and blockchain-based data management are set to revolutionize how companies secure online interactions.
- Greater Collaboration: Industries will increasingly work together—across automotive, industrial manufacturing, and even marketing—to create unified standards for digital security.
Businesses that take a proactive stance and integrate these measures into their daily operations will not only minimize the risk of disruptions but will also position themselves as leaders in their respective fields. The balance between ensuring robust cybersecurity and maintaining seamless user experiences will continue to pose nerve-racking challenges, yet those who manage to find their way through these twists and turns will likely emerge as the market innovators of tomorrow.
Embracing Change and Innovation
It is essential for business leaders to remain adaptable. The digital age requires continuous re-assessment of security protocols as technology evolves. Whether upgrading outdated systems or adopting cutting-edge innovations, deliberate and well-planned changes can ensure that businesses are not left on the back foot when it comes to cybersecurity.
Leaders can consider the following steps to stay ahead:
- Regular Risk Assessments: Continually review and update security policies to address emerging threats.
- Invest in Research and Development: Experiment with new digital tools and verification methods that enhance both security and user experience.
- Cross-Sector Collaboration: Engage with peers from different industries to share knowledge and develop improved strategies based on shared challenges.
By taking these proactive steps, business leaders can ensure that their organizations not only survive but thrive in an environment that is both unpredictable and dynamic.
Conclusion: Redefining Security in a Global Digital Era
In conclusion, the simple act of clicking a box to verify you’re not a robot is emblematic of broader themes that permeate today’s digital business landscape. This everyday digital prompt embodies the intricate relationship between convenience, security, and trust—a relationship that directly impacts small businesses, industrial manufacturing, automotive technology, economic policy, and marketing strategies.
As we have explored, the challenges associated with unusual activity detection and online verifications are filled with tricky parts and daunting twists. Business leaders must continue to work through these challenges by investing in reliable cybersecurity measures, training their teams, and embracing a culture of continuous improvement. In doing so, they not only shield their operations from potential threats but also build credibility and trust among customers and investors alike.
The journey toward a secure digital future is ongoing, and while it may be riddled with tense issues and confusing bits, it also offers tremendous opportunities for innovation and improvement. Whether you are managing a small business or spearheading industrial manufacturing processes, staying ahead of the curve in digital security can be a key differentiator in today’s competitive market.
Ultimately, as we adapt to this ever-changing landscape, it becomes clear that robust cybersecurity is not an optional add-on—it is a must-have element for success. In a world where economic trends, regulatory requirements, and technological advancements are evolving in tandem, the efforts we put into securing our digital interfaces today will serve as the foundation for a resilient and prosperous tomorrow.
By navigating through these confusing bits and managing your way around the challenges presented by new digital security requirements, you contribute to a safer, more trustworthy, and more innovative global economy. The message that once appeared as a minor disruption now stands as a call to action—a reminder that in the digital maze of today, every security step counts, and every business that adapts becomes a beacon of progress for the future.
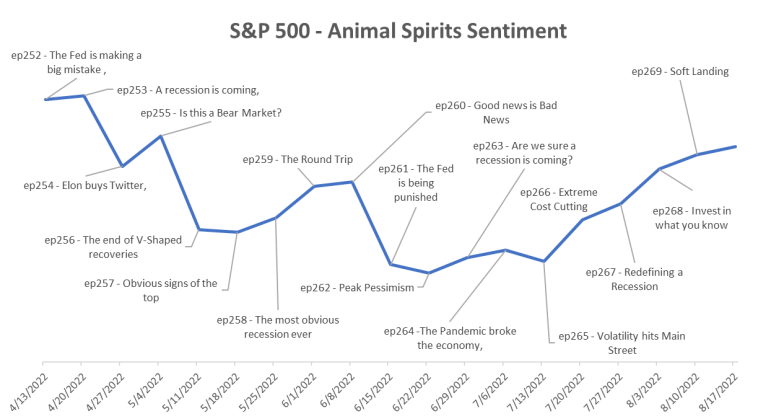
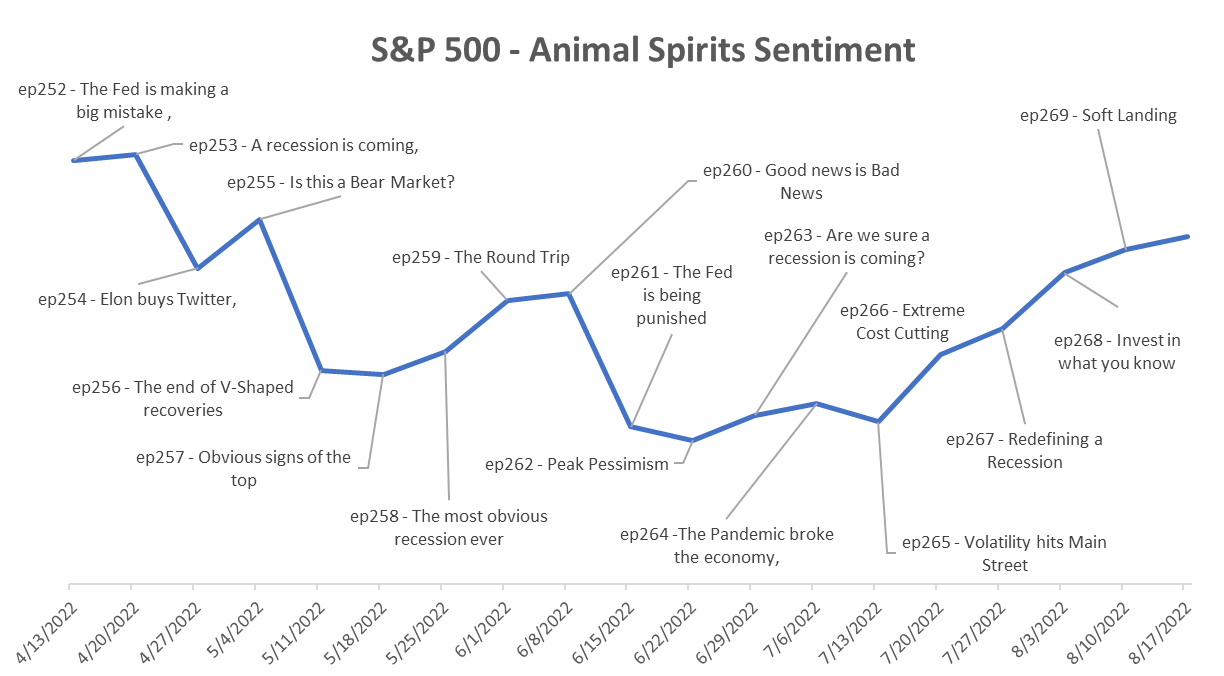
Originally Post From https://www.bloomberg.com/news/articles/2025-09-13/stock-market-rally-is-built-on-narrative-that-s-loaded-with-risk
Read more about this topic at
What happens if there’s an unusual sign-in to your account
Definition of “Unusual Activity Detected” – Microsoft Q&A